With Black Friday and Cyber Monday out of the way and the holidays right around the corner, IT folks are preparing to get the usual “new device” calls and helpdesk tickets. With over $9B spent on Black Friday itself, you can pretty much guarantee some of your co-workers got a new computer or mobile device. While bring your own device (BYOD) isn’t a new concept, enabling BYOD boosts employee productivity in several ways. The days when corporations would flatly ban the use of non-corporate-issued devices due to compliance reasons are waning, as most have seen the advantage of allowing users to bring their own devices and using them quickly and naturally at work.
Devices can be categories in two groups:
- Registered Devices are desktops (macOS, Windows, Linux) and mobile devices (iOS, Android) that have a Trusted Device Certificate in their keychain. These devices have been enrolled in the system and the organization/zero trust solution is aware of them. The Trusted Device Certificate also has information about the identity of the user that has enrolled the device, allowing for user and device identity to be part of the authentication and authorization equation.
- Unregistered Devices are desktops and mobile devices that do not have a Trusted Device certificate in their keychain. They may be unknown devices, especially the first time they are used.
Notice that we are not necessarily saying that an unregistered device is untrusted. We take a look at how unregistered devices can become “trusted” while on the path to becoming fully registered devices.
Organizations should have the ability to whitelist devices and then allow for self-service so that an end-user can get to corporate enrollment services or to specific services that are behind an identity-aware proxy. The whitelisting is accomplished by using the known, public IP address of the device. An end user can access sites like whatismyip.com and send their public IP address to an administrator. The admin will add the public IP address to the whitelist which will be used by security policies to allow this end user access only from that specific public IP. The addition of this IP address to the whitelist should ideally be temporary; to provide access to a resource while still “unregistered”, and being removed from the whitelist immediately afterward. We’ll discuss the benefits of registered devices later.
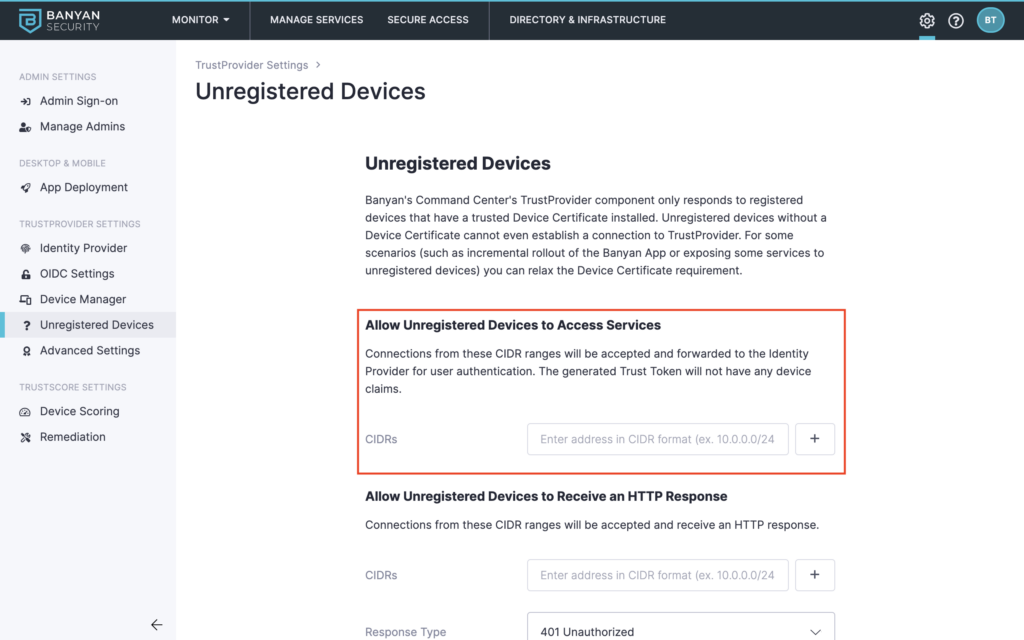
With the whitelist in place, the organization has the above option to enable the enrollment service access as well as the ability to create custom redirects to other services. These services may be for the enrollment with an Identity Provider (IdP) or multi-factor authentication (MFA).
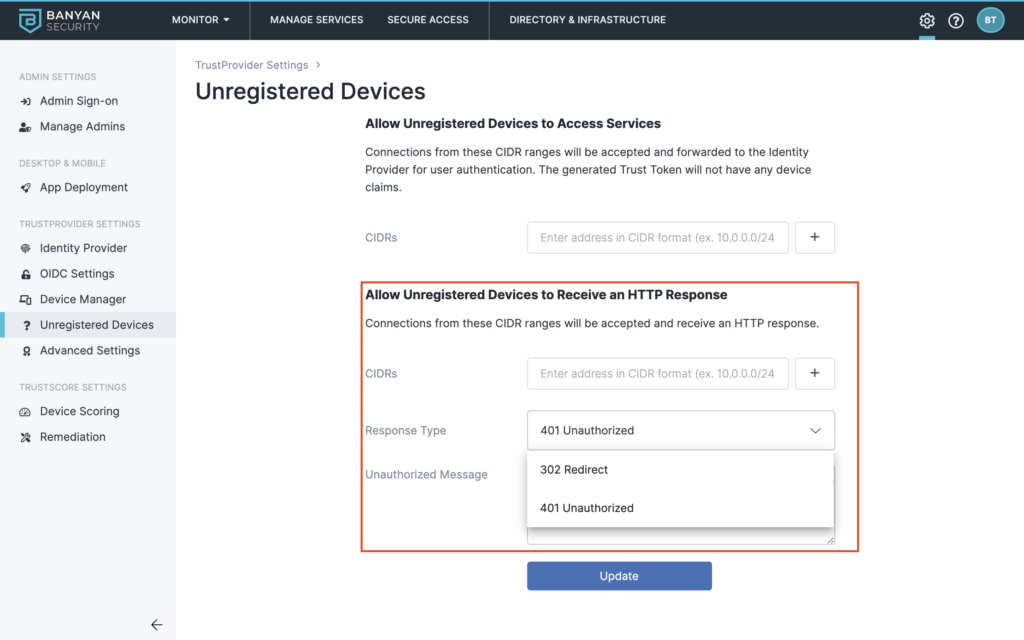
Moreover, some lower-risk services, may be made available for registered and unregistered devices based on a granular policy. Both types of devices will be visible to the administrator, along with the associated user.
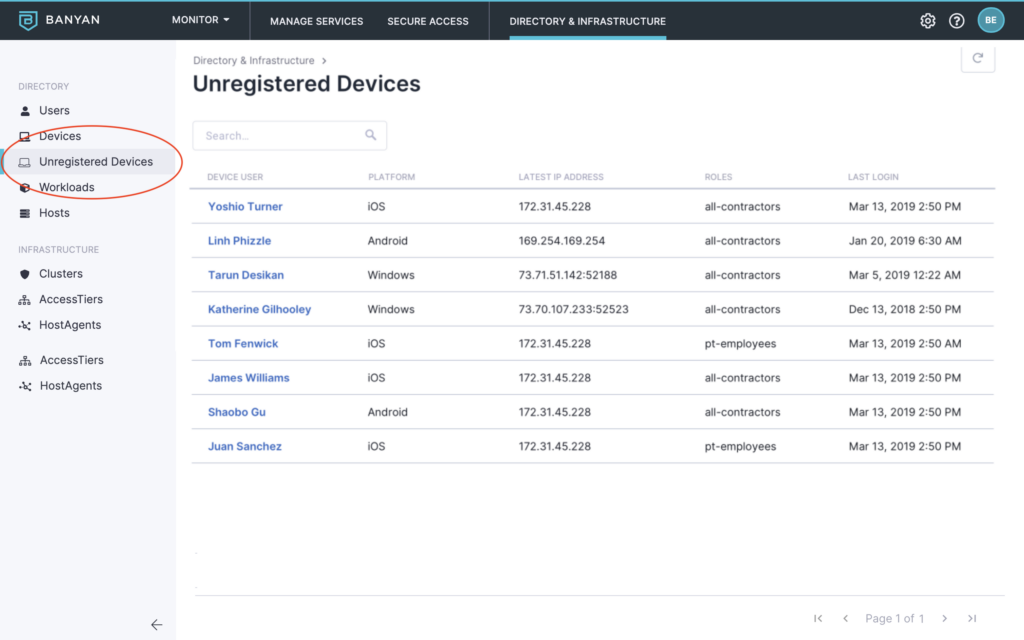
Enabling self-service to specific IP-source devices means enabling productivity quickly and will help most users avoid having to call IT to get help with new devices. As a best practice, you should always create policies that ensure that medium and high-risk resources are only accessible from known, registered, healthy, and compliant devices regardless of if they are BYOD or corporate-issued.
The ultimate goal should be to have all devices be registered, with the ability to allow unregistered devices as a pathway to that goal. Why? For the end user, having a registered devices means possibly getting access to additional resources that help them become more productive. Also, the Banyan app provides a Service Catalog that lets them know exactly what resources they can access. For the organization and the administrator, there are more possibilities for visibility and policy enforcement of those devices. Also, with our Remote Diagnostic functionality, which is built-in to the Banyan app, the admin can quickly address issues that may come up without requiring the end user to do anything to help in the troubleshooting.
To schedule a demo and see how easily you can support BYOD, visit https://www.banyansecurity.io/demo-request/.



