In this multi-part series, we’ll look at what organizations can do to better improve corporate cybersecurity as part of October’s Cybersecurity Awareness Month. In this blog, our focus is recognizing and reporting phishing.
Phishing (noun) – the fraudulent practice of sending emails or other messages purporting to be from reputable companies to induce individuals to reveal personal information, such as passwords and credit card numbers.
Your desktop, laptop, and mobile devices are being bombarded by phishing attempts all day long, typically through email and text messages. For the most part, your email and service providers are blocking 99.9% of attempts but as attackers change their methods, messages do get through. It is everyone’s job to recognize phishing and report phishing attempts.
Reporting phishing may mean clicking “Report Junk” so that the email provider’s anti-spam systems start blocking the messages, along with notifying others in your organization that a phishing attempt was sent.
Recognizing Phishing Attempts
Attackers give you many clues that can help you recognize a phishing attempt. We’ll look at some real examples to help you spot these clues. Before looking at the examples, it is worth noting that most organizations have specific, regular means of communicating, so if you receive a communication from some other non-standard means, you should be suspicious. Also, you should never be asked by your organization for passwords or passcodes via emails or text messages, so if you do get such a request for that information, you can be sure that those are phishing attempts.
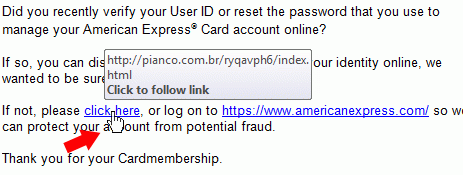
In the below email, you see an email from American Express. If you do not have an American Express account, this is obviously a phishing attempt. If you do have an American Express account, you will need to start looking for clues. The obvious indicator that this is a phishing attempt is that the links do not go to American Express websites. Even if the text, such as “click here” or “https://www.americanexpress.com/” may show a valid domain/website, when you hover over, you’ll see something else. In this case, the pianco.com.br site is a non-American Express site from Brazil. Brazil is known to host many suspicious services and command and control services. Do not ever click on these links.
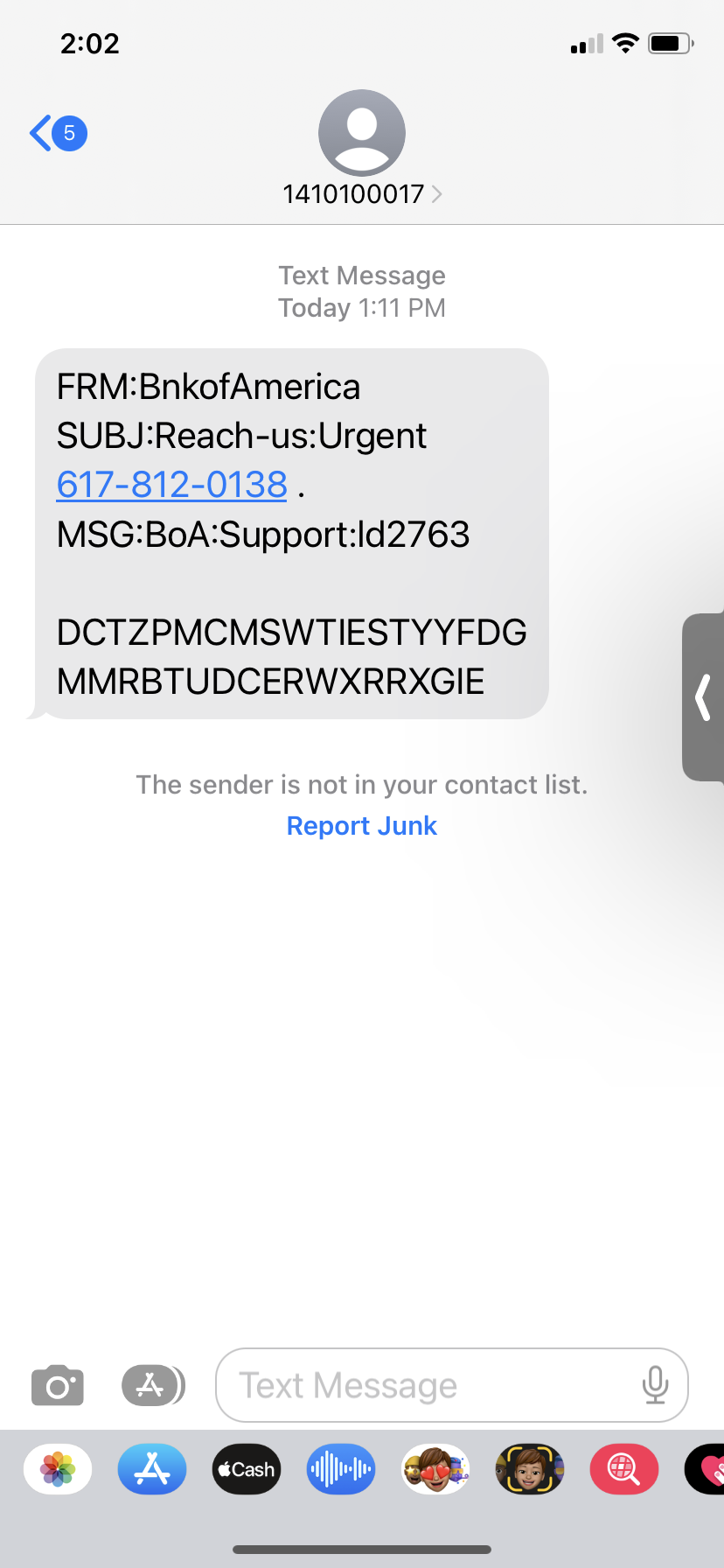
Next, we’ll look at a phishing text message. This message is supposed to be from Bank of America, so again, if you don’t have an account with B of A, you know it’s a phishing attempt. There are more clues. In this short message, you get a from and subject which usually aren’t in text messages. Also, Bank is mis-spelled as Bnk. Lastly, there is useless filler text which try to make it look like a confusing, automated message.
To report this phishing attempt, click on the “Report Junk” link to make sure your service provider knows that messages from this number are unwanted.
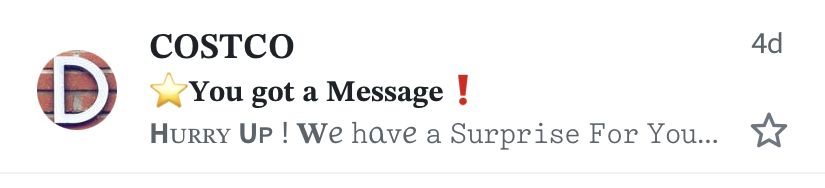
We’ll look at one final example of an email phishing attack. The sender is Costco, and again, if you don’t have a Costco account, you know right away that it’s a phishing attempt. In this email preview, you can find many clues that indicate that this is junk email or a phishing attack. Costco isn’t stylized correctly. Costco never writes their name in all caps as COSTCO. Also, the preview image on the left, which is a D means the email came from an address starting with D. Next, you can see that the subject is meaningless. It just says you got a message. Then it’s followed by a call to action (CTA), which wants you to hurry up.
Now let’s look at the email itself. The email is coming from a bogus, non-Costco email address. That should be enough to let you know it’s nefarious. The next clues are the obvious spelling mistakes like Costumer instead of customer. These emails are usually drafted overseas and aren’t reviewed. An email coming from a legitimate source will almost always look more polished, more professional, having been designed, reviewed and spell-checked by multiple people from that organization.

To summarize, try to look for clues to recognize phishing attempts. Do not click on any of the links or reply to any of the messages. Even replying with a rude message helps the attackers confirm that the email address is active. Lastly, once you recognize a phishing attempt, report it.
Stay safe and stay tuned for Part 5 in our series.



