Have you felt like you’re hearing more about spearphishing in the news? There’s a reason why: in the ever-expanding landscape of cyber threats, spearphishing has increased this year as a particularly insidious (but effective) tactic employed by threat actors to breach organizational defenses. From APTs to decentralized digital mercenaries, there are simply more attacks this year against more organizations, and the spearphisher is getting better at their job. According to Barracuda’s just-released 2023 Spearphishing Report, 50% of organizations have suffered spearphishing attempts during the past year.
Spearphishers from several APTs have been making headlines over the past few weeks due to increasing sophistication and the devastating consequences of their attacks, in several cases prompting multi-agency alerts to the U.S. cybersecurity community. Unlike traditional phishing attacks that cast a wide net, the latest spearphisher tactics (like those used by Iran’s Charming Kitten, North Korea’s APT43, and Kaminsky, which we’ll discuss below) are brutally targeted and increasing in their effectiveness. Worthy of note is how similar the tactics are between the APTs, despite being sponsored by different nation-states. Here are a few notable recent attacks over the past two months highlighting the severity of the spearphishing problem metastasizing through the cybersecurity corpus.
Charming Kitten Attacks, June 2023
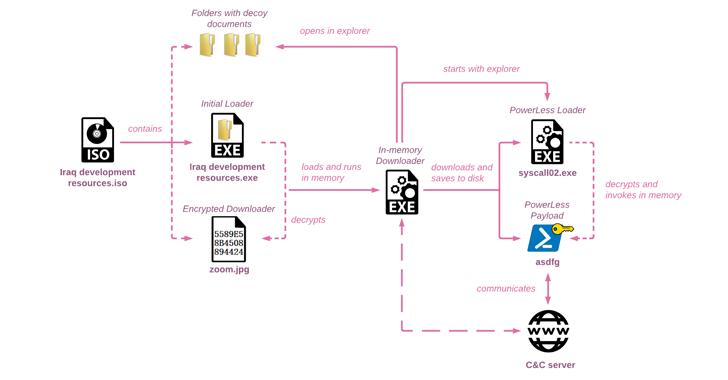
Volexity just published new research during the last week of June 2023 on the Charming Kitten APT group, an Iranian-based threat actor, who currently specializes in gathering intelligence through compromised credentials and spear-phishing emails. Once inside, the Charming Kitten APT group extracts additional access and attempts to shift to corporate VPNs or remote access services. In this particular spear-phishing campaign first observed in May 2023, Charming Kitten was found to be distributing an updated version of the POWERSTAR backdoor (aka CharmPower).
POWERSTAR Backdoor
Volexity analyzed the latest version of the POWERSTAR backdoor and discovered a complex POWERSTAR variant, likely assisted by a custom server-side component for automation.
Here’s how the attack played out: Charming Kitten spearphishers focused on a target using an email address while pretending to be an Israeli media reporter. Before deploying the malware via the pathways noted above, the spearphisher requested that the target review a document on US foreign policy (which is a common request from journalists to subject matter experts they have interviewed or might interview). Next, they sent a malicious LNK file embedded into a password-protected RAR file disguised as a “draft report” (along with the password).
The Charming Kitten Spearphisher Playbook
Here is how the spearphishing attack unfolds:
- The spearphisher poses as a genuine person with a verifiable public profile, initiating contact and establishing a basic rapport with the target.
- The sender’s email is a lookalike of the impersonated person’s personal account, disguised by a reputable webmail service. The first contact contains no malicious content, avoiding security software detection and recipient concerns (“There’s no link or attachment…this email must be safe…”)
- After getting a reply from the target, the spearphisher follows up with emails strengthening the attacker-victim rapport and trust.
- Spearphisher emails a malicious, password-protected attachment, separating the password to restrict automated scanning and extraction.
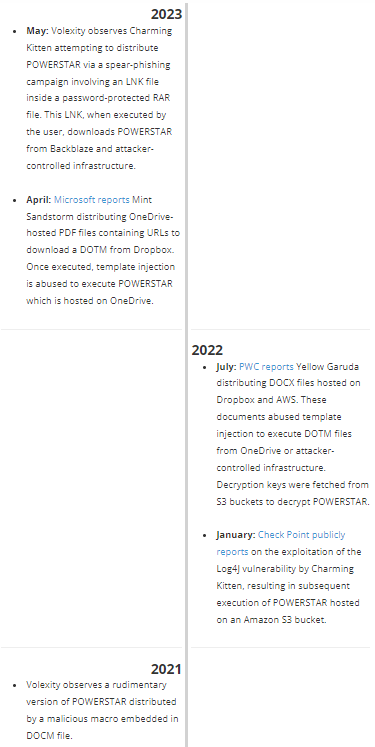
Charming Kitten – Not so Powerless
Earlier in April, Charming Kitten was also observed spearphishing Israeli targets with malware designed to deploy an updated version of a Windows backdoor called PowerLess.
Here’s where the attack chain starts: an ISO disk image file equipped with Iraq-themed lures to drop a custom, in-memory downloader that in turn launches the PowerLess implant. The ISO file displays a decoy document written in Arabic, English, and Hebrew, and appears to discuss academic content about Iraq from a legitimate non-profit entity called the Arab Science and Technology Foundation (ASTF), hinting that the research community itself may have been the original campaign target.
The PowerLess backdoor steals data from web browsers and apps like Telegram, logs keystrokes, takes screenshots, and records audio. According to Check Point: “while the new PowerLess payload remains similar, its loading mechanisms have significantly improved, adopting techniques rarely seen in the wild, such as using .NET binary files created in mixed mode with assembly code. PowerLess [c2] communication to the server is Base64-encoded and encrypted after obtaining a key from the server. To mislead researchers, the threat actor actively adds three random letters at the beginning of the encoded blob.”
Spearphisher Team: APT 43 + Kimusky
Charming Kitten isn’t the only APT using this nefarious tactic of impersonating others to launch spearphishing campaigns. At the end of May 2023, Mandiant reported the existence of a new self-funding advanced persistent threat, APT 43, whose activities overlap with that of Kimusky (and sometimes have been attributed to that group). In early June 2023, the NSA advised that Kimusky (also known as Thallium, or Velvet Chollima) has been conducting large-scale espionage campaigns against members of think tanks, academia, and media. Kimsuky spearphishers meticulously plan, then execute their attacks with email addresses that closely resemble those of real individuals, then by crafting convincing, realistic content for the intended target.
Like Charming Kitten, the spearphisher impersonates legitimate, unknowing journalists or writers to inquire about topics like current political events in the Korean peninsula, pending U.S. talks, or foreign or economic policies with China. Emails contain inquiries, invitations for interview, an ongoing survey, or requests to review documents and reports. Similar to Charming Kitten, the initial emails are usually free of malware or any attachments, as their role is to gain the target’s trust rather than achieve a quick compromise. The detailed steps from their playbook below are excerpted from the joint June US Government advisory below.
The Kimusky Spearphisher Playbook
- Kimsuky actors are known to impersonate well-known news outlets and journalists using a domain such as “@XYZcnn.news,” spoofing a real news outlet, while actual emails from the news service appear as “@XYZnews.com.”
- DPRK cyber actors commonly take on the identities of real people to gain trust and establish rapport in their digital communications. Kimsuky actors may have previously compromised the email accounts of the person whom they are impersonating. This allows the actors to search for targets while scanning through compromised emails, with a particular focus on work-related files and personal information pertaining to retirees, social clubs, and contact lists. They craft convincing spearphishing emails by repurposing the person’s email signature, contact list, and past email exchanges. DPRK cyber actors are also known to compromise email accounts belonging to foreign policy experts and subsequently create a secondary email account, using the email account and identity of the expert to communicate with other significant targets.
- In other cases, a Kimsuky actor will use multiple personas to engage a target; one persona to conduct initial outreach and a second persona to follow-up on the first engagement to distract a potential victim from discerning the identity of the original persona. Another tactic is to resend” or “forward” an email from a source trusted by a target.
- The initial phishing email occasionally contains a malicious link or document, often purporting to be a report or news article. These attached malicious documents are frequently password-protected, which helps them evade detection by antivirus software and other security measures. However, more often, the initial spearphishing email does not contain any malicious links or attachments and is instead intended to gain the trust of the victim.
- Once DPRK cyber actors establish engagement with a target, the actors attempt to compromise the account, device, or network belonging to the target by pushing malicious content in the form of a malicious macro embedded within a text document. This document is either attached directly to the email, or stored in a file hosting service, such as Google Drive or Microsoft OneDrive. These malicious macros, when enabled, quietly establish connections with Kimsuky command and control infrastructure, and result in the provision of access to the target’s device.
- In some cases, Kimsuky actors have developed “spoofed” or fake but realistic versions of actual websites, portals, or mobile applications, and directed targets to input credentials and other information that are harvested by the DPRK. Compromise of a target account can lead to persistent access to a victim’s communications, often through a malware used by Kimsuky actors called BabyShark. Kimsuky actors have also been known to configure a victim’s email account to quietly auto-forward all emails to another actor-controlled email.
It’s worth keeping an eye on these spearphishing tactics coming out of the APTs (especially those listed above), mostly because attacks get tested in one environment before the tactics spread; often an APT tries a strategy in one place against one target, and then they (or their counterparts and competitors) perfect the techniques and weaponize them further. The same tactics executed against academics one day often take down industrial control systems or enterprises in subsequent months once other cybercriminals find them effective.
A recent talk I attended at Seattle BSides 2023 comes to mind discussing an intrusion from one of the APTs listed above into a volatile manufacturing environment, where the consequences of two chemicals mixing at the wrong time would have been lethal not just to occupants of the factory, but the town in which the plant was housed. We all know cybersecurity has implications in the physical world, but the data shows the spearphisher has gotten smarter…and so should your defensive tools.
Learn more about how Banyan protects against the evolving threat landscape and schedule a custom demo today.
*Researched and authored by Mademoiselle