
We’re excited to announce the latest capability in the Banyan Zero Trust Remote Access Platform – One-Click Server Access for Developers. Banyan Security provides you with a modern alternative to the stack of traditional security tools – such as VPNs, bastion hosts, firewalls and authentication agents – that are used today to manage server access. Enterprise IT teams can give their developers a great SSH user experience and reduce the overall operational burden of provisioning access to server infrastructure, all while enhancing corporate security posture. In this article, we’ll explain why we built this feature, dive into how it works and describe how customers use it to roll out secure cloud operations processes.
Traditional SSH Access Control Techniques Fail in Today’s Remote-first Cloud-first World
Secure Shell (SSH) is the industry-standard remote administration protocol for servers. For today’s fast-moving engineering teams building and managing software across various cloud environments, SSH is a widely used mission-critical tool.
Yet, techniques to secure server access using SSH have hardly changed in the past 20-odd years.
 Most organizations use a sequence of VPNs, bastion hosts, and firewalls to manage network connectivity from user to server. Then, they use some combination of directory services and authentication managers to manage credentials so the user can authenticate into the server itself.
Most organizations use a sequence of VPNs, bastion hosts, and firewalls to manage network connectivity from user to server. Then, they use some combination of directory services and authentication managers to manage credentials so the user can authenticate into the server itself.
Things were set up this way because each tool was designed for a specific purpose:
- VPN – network connectivity, so the user can tunnel over an insecure network
- Bastion host – SSH protocol-aware logging and detailed audit trails
- Firewall – network segmentation to restrict the broad network access granted by VPNs and bastions
- Directory services – authenticate the user via username and password
- Authentication manager – provision groups, keys, machine configurations
While this works up to a point, it’s a lot of security tools to manage, each with its own provisioning policies and management framework. Worst of all, each of these security tools has major blind spots and is typically not aware of the next one in the chain:
- VPN – provides users complete access to a network, isn’t aware of user, device, or application context
- Bastion host – is difficult to manage, cannot be exposed to the internet, and delivers a poor user experience
- Firewall – uses CIDR-based segmentation rules that get complex very quickly
- Directory services – designed to use static credentials that are easily compromised
- Authentication manager – relies on expensive server agents that typically involve high management overhead
Many enterprises today run across multiple datacenter and cloud IaaS environments. Deploying this entire security stack across a multi-cloud infrastructure further compounds the problems. Organizations often also reserve the full security stack only for production environments, leaving non-production environments particularly vulnerable to attack.
And, finally, think of the unfortunate developer who must jump through all of these hoops just to log onto a server to check on some application logs. It can be an immensely frustrating experience where a simple security rule misconfiguration can cause hours of lost productivity.
A Modern Approach to Server Access
Fortunately, there are much better ways to manage server access. Cloud-native stalwarts, including Facebook, Netflix, and Uber, have all developed and open-sourced different homegrown setups that replace much of these traditional security controls with modern alternatives. While each approach is different, they do share some common underlying themes:
- An enterprise-grade Public Key Infrastructure (PKI), with the ability to issue client and server certificates
- API-driven automation so short-lived certificates can be provisioned on-demand to servers and users
- Centralized entitlement management, tied to a cloud-based identity provider
- Centralized security policy management, tied to other enterprise security tools
- Distributed enforcement that can span multiple private networks and clouds
This list is fairly daunting and few enterprises can dedicate the technical resources needed to build and roll out such types of access control systems for their developers. Modern server access capabilities have thus been out of the reach of most enterprises. Until now!
A Comprehensive Server Access Solution
Banyan Security’s new Zero Trust for SSH feature enables enterprise IT teams to do away with several traditional security tools and manage server access securely, all while ensuring a great developer experience.
Banyan’s three core product components work in concert to enable this capability:
- Desktop App (Windows, macOS, Linux) – runs a user space local proxy that sets up MTLS connectivity on-demand using short-lived certificates
- Cloud Command Center – a SaaS platform that lets you write Zero Trust policies and manages your PKI infrastructure
- Distributed Access Tier – enforces security policies and sets up a TCP connection to a specific server, without granting broad network access
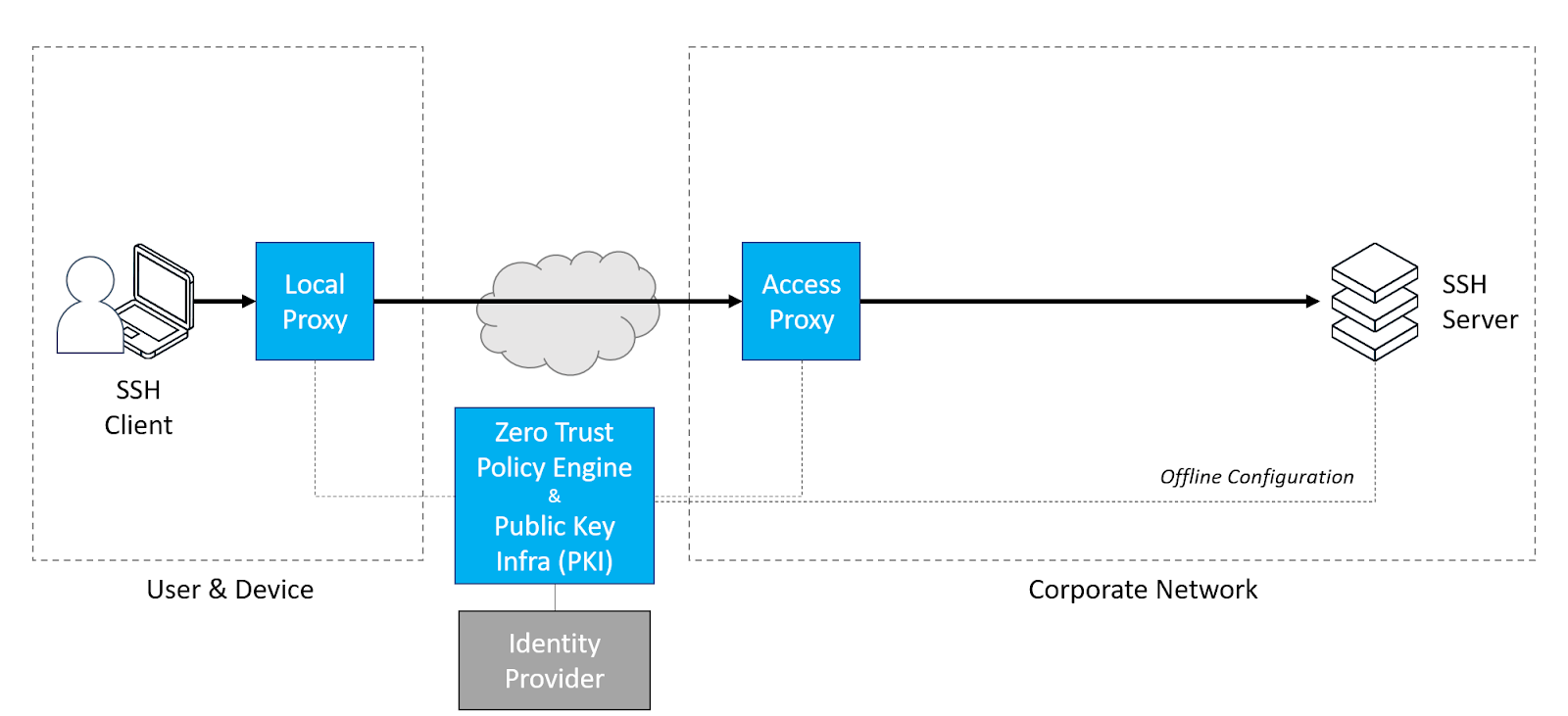
With the Banyan SSH solution, you benefit from a Zero Trust security posture, where the user and device are explicitly authenticated and access is granted only for the specific server (without broad network access). By leveraging the organization’s IDP for authentication and issuing short-lived certificates with the user’s entitlements, Banyan sets up connectivity on-demand and eliminates the risk associated with static passwords and credential leakage. Banyan’s real-time Trust Scoring enforcement allows for dynamic security policies that can be customized based on the sensitivity of server environments.
You also simplify IT operations and achieve a great developer user experience. Unlike other solutions on the market, Banyan’s approach requires no server agents, just a one-time offline configuration. Comprehensive audit logging and session recording can be enabled via configuration options. Best of all, users can retain their existing SSH clients and development workflows, relying on “just in time” provisioning to get on-demand access to the servers they need to do their job.
See Banyan in Action
In the demo video below, a user has registered their device via the Banyan app. With the click of a button the user gets provisioned “just-in-time” on the server and is able to log in.
In order to deliver this single-click user experience, Banyan performs several steps under the hood, transparent to the user:
- Obtain short-lived X.509 and SSH certificates via authentication with the IDP
- Set up a secure MTLS tunnel with the access proxy
- Validate the user’s roles and TrustScore service policies configured in the Banyan Command Center
- Provision the user just in time via an SSH certificate and utilize OpenSSH’s authorized principals capabilities to manage role-based access to the server
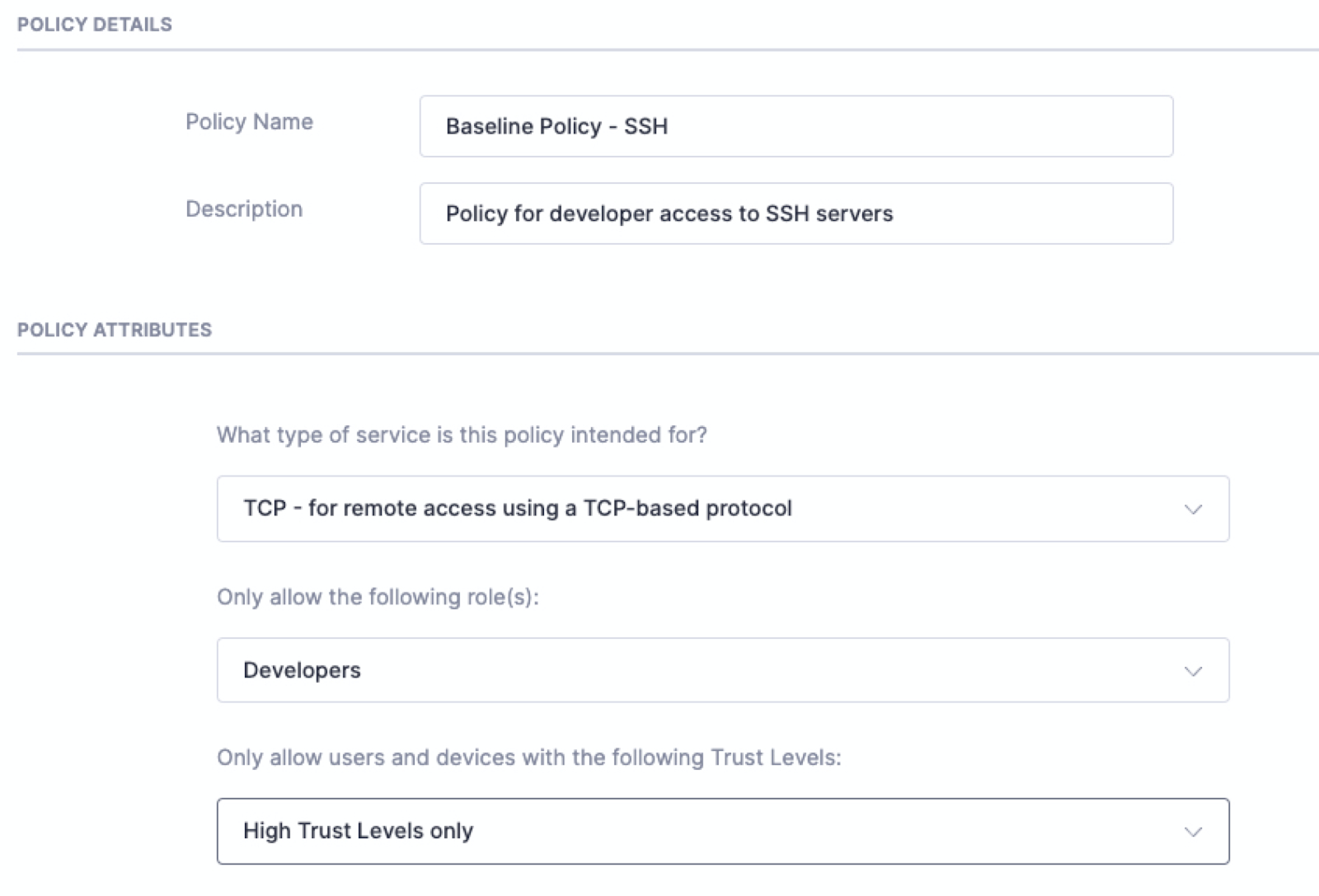
(Policy in Banyan indicating only developers with High Trust can access SSH servers)
And there you have it, secure server access granted! For trusted users on trusted devices, Banyan provides access to SSH servers across datacenters and clouds with one click. No VPNs, bastion hosts or authentication managers needed.
Banyan and Continuous Authorization
No Zero Trust story is complete without continuous authorization and enforcement! (Learn why here)
Many Zero Trust solutions focus heavily on authentication and ensuring some level of user or device validation prior to accessing a service, but that’s only half the battle. Once a user is through the proverbial door, you have to be able to ensure real-time trust and be able to revoke access instantaneously once a threat has been posed. This is no simple feat. It involves correlating data not only from the user and device but also from existing security investments such as identity providers, device managers, and endpoint detection and response tools.
Now let’s say the user removes CrowdStrike from their device. Within a few seconds, their Banyan TrustScore drops to 0 and active SSH sessions are terminated! The Banyan app provides the end user with self-remediation steps that they can perform via the Banyan app to increase their TrustScore and regain access.
For administrators, audit logging shows details on both the Authorize and Revoke events. Advanced logging within OpenSSH can also be enabled for live session auditing.

Get Started Today with Zero Trust for SSH
To enable one-click SSH access for your development teams, simply log into the Banyan Command Center, register a Service of type “SSH” and map it to the appropriate servers. Your organization’s developers get the benefits of one-click access while admins get the peace of mind that their security policies are granular enough to protect backend resources…continuously.



