The Banyan Security Platform offers industry-leading Zero Trust Network Access (ZTNA) capabilities that protect company resources by enabling least-privilege access to hosted applications and infrastructure based on real-time contextual factors including user and device trust scoring and resource sensitivity. In short, Banyan safely and securely enables “Work From Anywhere” for the modern, hybrid enterprise where remote and on-premises access are equally important.
Infrastructures grow ever more complex, with applications spread across on-premises, hybrid, and multi-cloud environments. Traditional network-centric solutions like legacy VPNs have been put to the test and revealed significant performance, usability, and systemic security issues that band-aids cannot fix. To address these realities, a scalable and comprehensive approach to secure remote access is required.
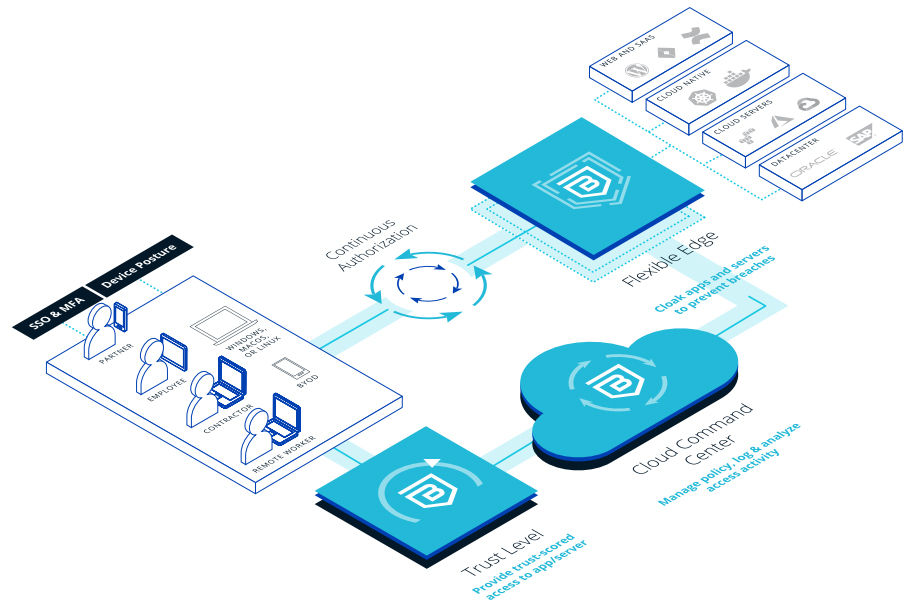
The Banyan Security Platform leverages a robust trust-scoring methodology during initial authentication and continuously re-authorizes access based on real-time contextual information, including telemetry from existing security tools. The Banyan Flexible Edge cloaks all corporate assets and provides secure granular or global access within policy guidelines. The Cloud Command Center provides clear visibility and audit capabilities for IT teams to set and monitor those policies and responds in real-time to changing trust scores.
Why Banyan
Easy to Deploy & Use
Unmatched Security

Actionable Insight
Banyan provides actionable insights through deep visibility into user, device, app, and service activity, permitting superior control and accountability. Automatic Discover & Publish capabilities, for example, make it a snap to know what’s available to be published.
How Banyan Works
Zero Trust Access Use Cases
Modernize / Replace Legacy VPN
Protect company resources by enabling least-privilege access to specific applications and servers based on the combined real-time contextual factors of user and device trust scoring and resource sensitivity. Deploy incrementally – alongside existing infrastructure, if desired.
Support Third-Party Access / BYOD / M&A
Provide third-parties easy, secure access to only the specifc resources they need, optionally incorporating device trust (below). Enable BYOD without needing Mobile Device Management (MDM) or Unified Endpoint Management (UEM). Corporate assets are continuously protected while delivering an enhanced user experience that doesn’t require control of users’ preferred devices.
Device Trust & Posture
Device trust complements user trust by uniquely identifying each device and quantifying its posture. Granular Trust-Based Access Control policies enable enforcement of user and device identity, device posture, and resource sensitivity, reducing the risk of credential loss and theft.
Free for 30 Days
Simple, secure, & free!
Quickly provide your workforce secure access to corporate resources and infrastructure.
